Intel has verified that a resource code leak for the UEFI BIOS of Alder Lake CPUs is authentic, elevating cybersecurity issues with researchers.
Alder Lake is the title of Intel’s 12th technology Intel Main processors, launched in November 2021.
On Friday, a Twitter person named ‘freak’ posted links to what was said to be the supply code for Intel Alder Lake’s UEFI firmware, which they declare was released by 4chan.
The website link led to a GitHub repository named ‘ICE_TEA_BIOS’ that was uploaded by a person named ‘LCFCASD.’ This repository contained what was explained as the ‘BIOS Code from job C970.’
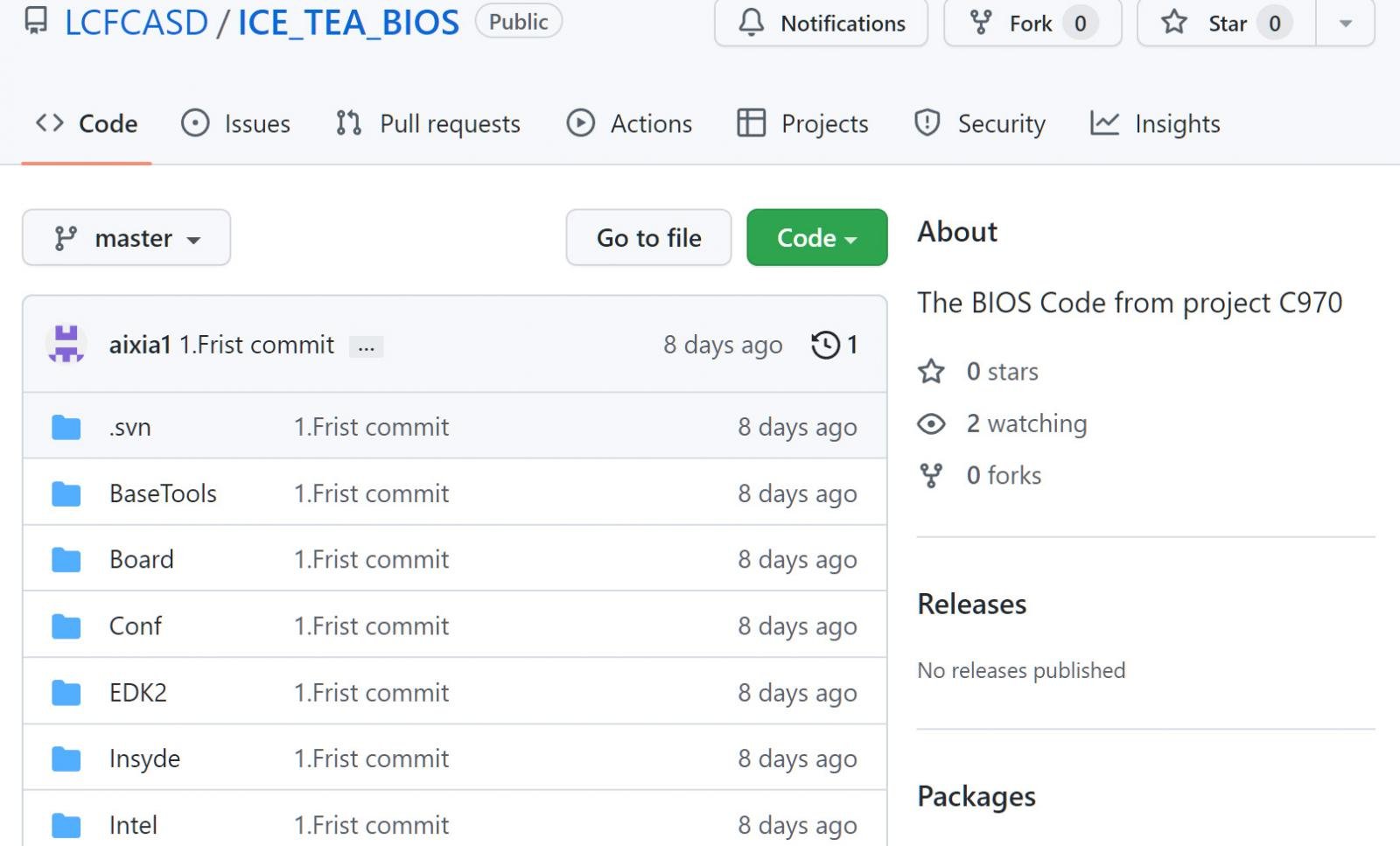
Resource: BleepingComputer
The leak contains 5.97 GB of documents, source code, non-public keys, transform logs, and compilation equipment, with the most recent timestamp on the information getting 9/30/22, likely when a hacker or insider copied the details.
BleepingComputer has been advised that all the source code was designed by Insyde Application Corp, a UEFI technique firmware advancement firm.
The leaked source code also is made up of various references to Lenovo, together with code for integrations with ‘Lenovo String Service’, ‘Lenovo Protected Suite’, and ‘Lenovo Cloud Services.’
At this time, it is unclear whether or not the source code was stolen throughout a cyberattack or leaked by an insider.
Having said that, Intel has confirmed to Tom’s Hardware that the resource code is genuine and is its “proprietary UEFI code.”
“Our proprietary UEFI code seems to have been leaked by a third bash. We do not believe that this exposes any new protection vulnerabilities as we do not count on obfuscation of information as a security measure. This code is lined underneath our bug bounty program in the Undertaking Circuit Breaker campaign, and we really encourage any researchers who may possibly identify probable vulnerabilities to carry them our interest by means of this application. We are achieving out to the two shoppers and the stability research local community to preserve them knowledgeable of this situation.” – Intel spokesperson.
Protection scientists anxious
Though Intel has downplayed the security threats of the source code leak, safety scientists warn that the contents could make it less difficult to uncover vulnerabilities in the code.
“The attacker/bug hunter can massively benefit from the leaks even if leaked OEM implementation is only partially utilised in the creation,” explains hardware safety company Hardened Vault.
“The Insyde’s resolution can help the safety researchers, bug hunters (and the attackers) discover the vulnerablity and fully grasp the outcome of reverse engineering very easily, which adds up to the lengthy-term significant danger to the buyers.”
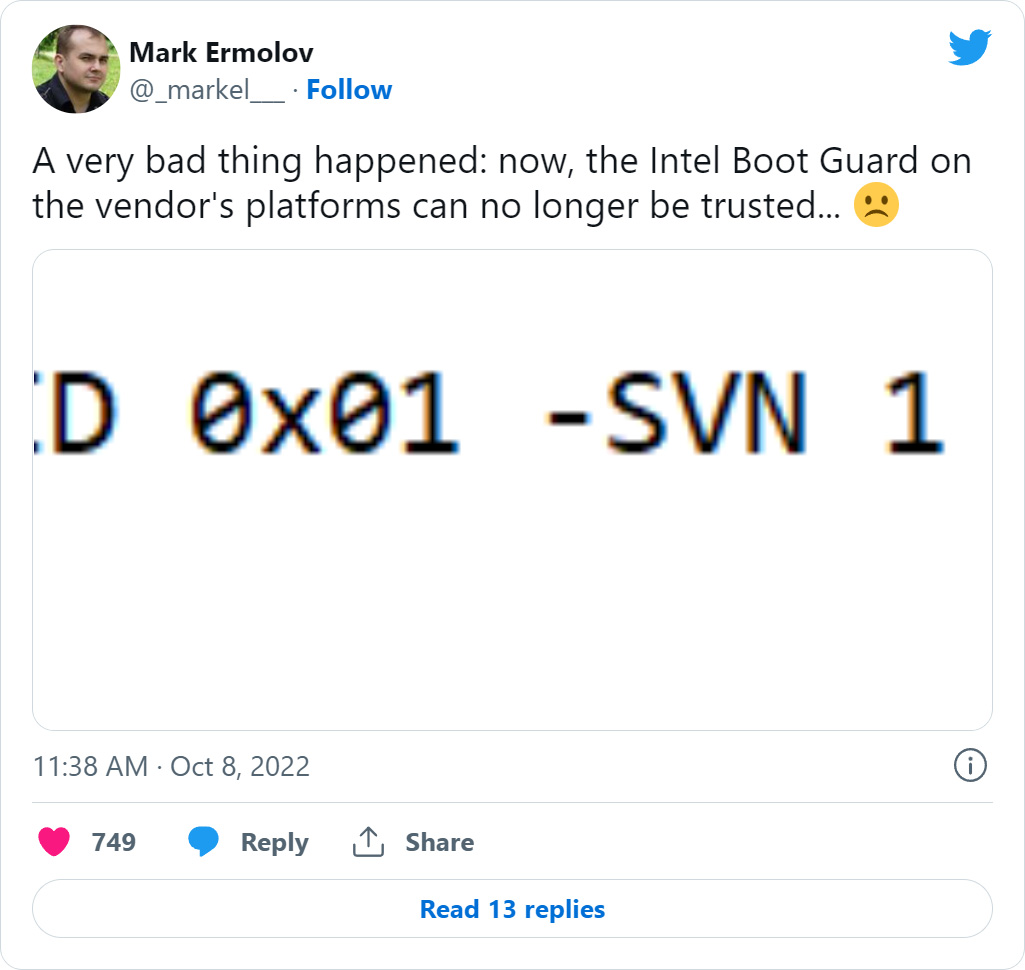
Optimistic Systems components researcher Mark Ermolov also warned that the leak bundled a KeyManifest private encryption essential, a personal important applied to protected Intel’s Boot Guard system.
Although it is not very clear if the leaked private vital is utilised in output, if it is, hackers could most likely use it to modify the boot policy in Intel firmware and bypass hardware security.
BleepingComputer has contacted Intel, Insyde, and Lenovo with queries about the leak and whether or not the private keys had been made use of in creation.
We will update this posting with any responses as we study more.